Atomic macOS Stealer AMOS malware: In a concerning development, the ‘ClearFake’ browser update campaign has reached macOS, targeting Apple computers with the Atomic Stealer (AMOS) malware.
The narrative began unfolding in July of this year, with ClearFake initially focusing on Windows users. Using deceptive Chrome update prompts on compromised websites through JavaScript injections, the campaign took off on a troubling note.

Fast forward to October 2023, Guardio Labs uncovered a significant evolution in the campaign. The perpetrators employed Binance Smart Chain contracts and a technique called “EtherHiding” to conceal malicious scripts within the blockchain. This led to tailored payloads for Windows systems, featuring information-stealing malware like RedLine, Amadey, and Lumma.
The plot thickens as ClearFake extends its reach to macOS. On November 17, 2023, Ankit Anubhav, a threat analyst, raised the alarm, revealing that ClearFake had escalated its tactics by distributing DMG payloads to macOS users on compromised websites.
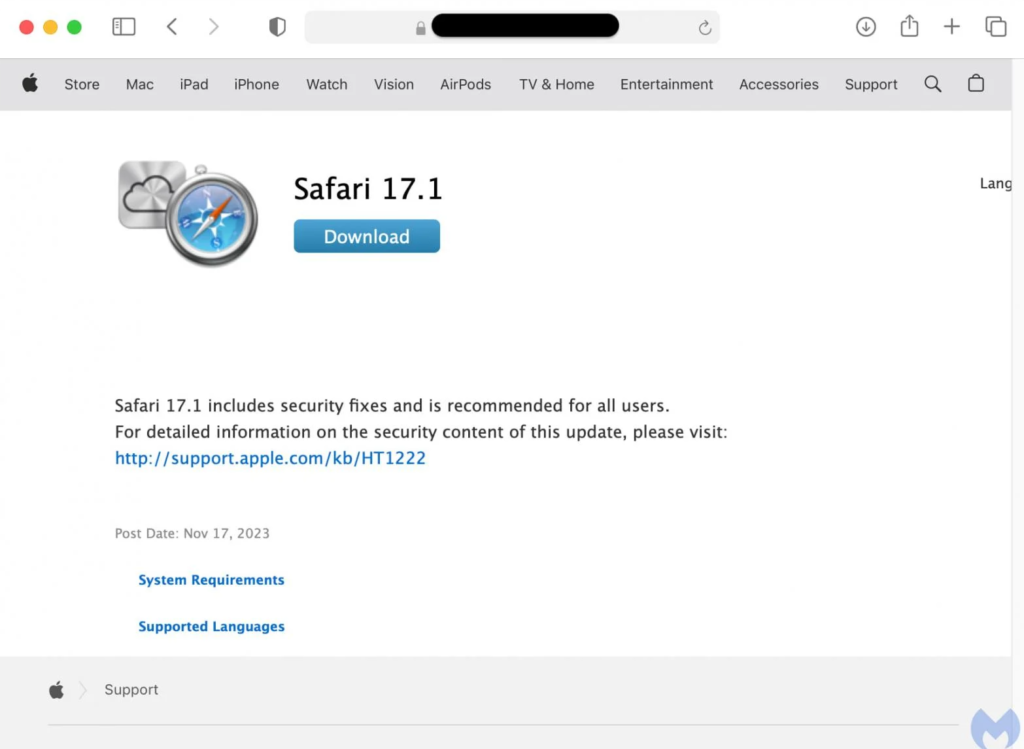
A recent report from Malwarebytes sheds light on the severity of the situation, revealing that these attacks not only involve the standard Chrome overlay but also use a Safari update lure. The weapon of choice is Atomic—an information-stealing malware sold to cybercriminals through Telegram channels for $1,000 per month.
Discovered in April 2023 by Trellix and Cyble, Atomic is designed to steal passwords, cookies, credit card details stored in browsers, and data from over 50 cryptocurrency extensions and keychain passwords.
For Apple users, the expansion of the ClearFake campaign to target Macs serves as a reminder to bolster security measures and exercise caution during downloads, especially when prompted to update browsers while browsing.
Despite months passing since the discovery of Atomic, it remains undetected by around 50% of antivirus engines on VirusTotal.
A crucial note for users: Safari browser updates will exclusively come through macOS’s Software Update. Updates for other browsers will be managed directly within their interfaces. Any prompts on websites urging browser updates should be treated with skepticism and promptly dismissed.
The compromise of the keychain password, the heart of macOS’s security, can unlock WiFi passwords, website logins, credit card data, and other encrypted information. An examination of the payload’s strings by Malwarebytes reveals a series of commands crafted to extract sensitive data, including passwords, and target document files, images, crypto wallet files, and keys.
In this digital landscape where threats can arise unexpectedly, vigilance is our greatest shield. Stay informed, stay cautious, and let’s navigate the online world with our guard up as a collective effort.

