HrServ Web Shell: In a digital landscape filled with complexities, a clandestine player has emerged, deploying an enigmatic web shell named HrServ in a suspected advanced persistent threat (APT) assault against an undisclosed government entity in Afghanistan.

This elusive web shell, donned with the cryptic moniker “hrserv.dll,” reveals a sophisticated nature, boasting advanced functionalities such as bespoke encoding methods for client communication and seamless in-memory execution. Unveiling these intricacies is the vigilant eye of Kaspersky security researcher Mert Degirmenci, whose recent analysis peels back the layers of this cybernetic intrigue.
Diving into the depths of this digital mystery, Kaspersky has unraveled the timeline of this malware, exposing variants dating back to the early tendrils of 2021. The fingerprints of its presence are discerned through the careful scrutiny of compilation timestamps, allowing us a glimpse into the evolution of this elusive threat.
Web shells, those covert malefactors of the cyber realm, act as insidious tools, granting remote dominion over compromised servers. Their nefarious repertoire includes acts of data pilferage, vigilant server surveillance, and the surreptitious dance of lateral movement within the intricate web of networks.
The narrative of this cyber saga takes an intriguing turn with the unveiling of the attack sequence. A tale woven with the threads of technology, the PAExec remote administration tool takes center stage as a nimble alternative to PsExec. Like a chameleon, it assumes the guise of a Microsoft update (“MicrosoftsUpdate”), concealing its true identity. Its purpose is clear — to set in motion a Windows batch script (“JKNLA.bat”).
This script, with the DLL file (“hrserv.dll”) as its guide, births an HTTP server. A sentient entity capable of deciphering the language of incoming requests, interpreting nuances within HTTP requests through the activation of specific functions signaled by GET parameters, including the cryptic ‘hl’ that mirrors the facade of Google services.
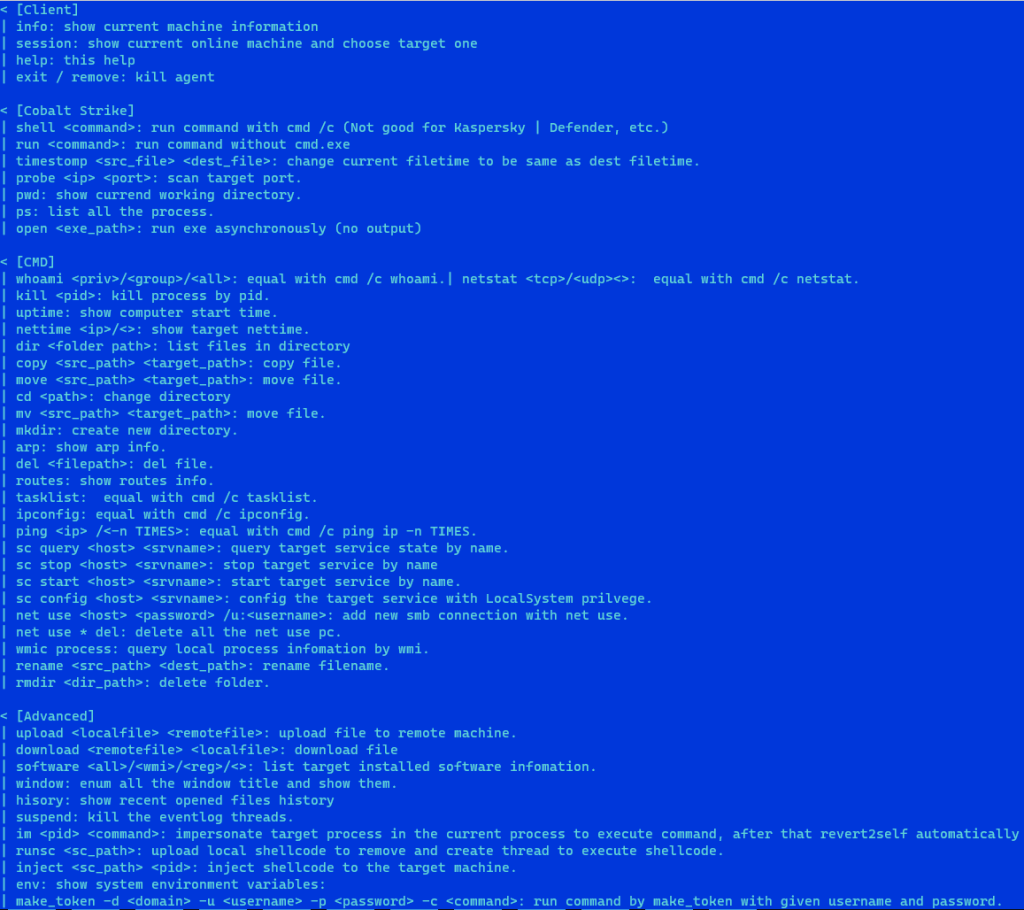
The malicious requests, akin to ghosts in the digital mist, strive to assimilate into the ebb and flow of network traffic. Their aim? To blur the lines between malicious intent and the innocuous hum of everyday events.
In the lexicon of HTTP requests, a parameter named “cp” holds the key. With values oscillating between 0 and 7, it dictates the unfolding narrative — spawning threads, crafting files with arbitrary data, perusing files, and delving into the sanctum of Outlook Web App HTML data.
The plot thickens when the elusive “6” surfaces in the POST request. A signal that triggers a symphony of code execution, decoding encrypted data, transplanting it into the memory, birthing a new thread, and lulling the process into a slumber.
As if the web shell were a maestro orchestrating a digital opera, it unveils yet another act. A discreet “multifunctional implant” emerges from the wings, erasing its digital footprints with surgical precision. The “MicrosoftsUpdate” job, the initial DLL, and the script files vanish, leaving behind a void in the digital tapestry.
The identity of the enigmatic threat actor remains shrouded in mystery. A linguistic trail of breadcrumbs suggests a non-native English speaker as the puppeteer behind this digital marionette.
In the denouement, Degirmenci, the virtual detective of this cyber saga, draws his conclusions. Despite the earmarks of financially motivated malice, the operational choreography of this digital ballet bears a striking resemblance to the orchestrated moves of an Advanced Persistent Threat (APT). The plot thickens, and the digital veil remains lifted only slightly, revealing fragments of a story written in the intricate language of cyber warfare.
Based on the TTPs (Tools Techniques and Procedures) analysis, it was found that the new variant was different from the new one. Further, the analysis found that language was set to English but search results should be shown in Chinese. The shown is the old variant url (Information Source).
https://+:443/owa/MSExchangeService.svcThe new variant sample with language set to Chinese shown below.
&cp=1&client=desktop-gws-wiz-on-focus-serp&xssi=t&hl=en-TW&authuser=0&pq=The new variant is capable of initiating in-memory execution and can start communication by exploiting temporary and registry files.

