Amid the RAT market grows among the hackers, a new variant of Bandook RAT has been found to target Windows Machines. This new variant makes it way through the phishing attacks to bypass the all the securities walls, aiming to get inside the victim’s windows machine.
Table of Contents
Introduction to Bandook RAT
According to the Fortinet FortiGuard Labs, the activity was observed in October 2023. During that time the malware was getting distributed via malicious PDF file. Inside the PDF file, there use to be an embedded link to a .7z archive with password protection.
Pei Han Liao, a security researcher at Fortinet has showcase the entire research and said that malware injects the payload into “msinfo32.exe” of victim’s machine after the file gets extracted from the .7z compressed folder.
The 2007 variant of Bandook RAT has various features to infect system and gain remote control over the victim’s machine. According to security researcher Pei Han Liao, the previous variant use to create 4 registries into windows machine but the latest variant is much advanced does the job very easily.
Bandook RAT Modus Operandi
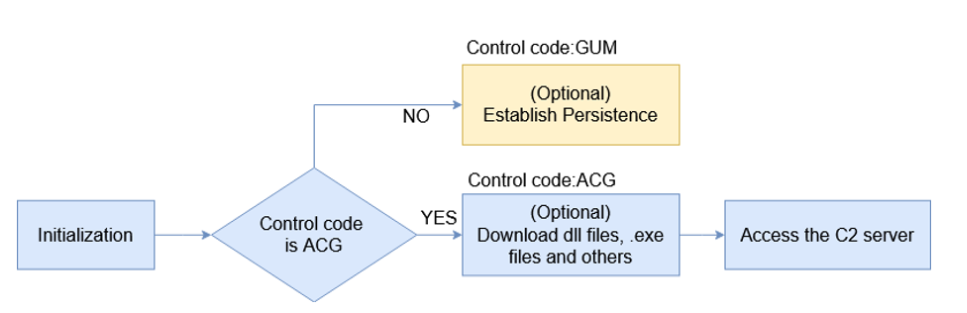
If we look at the modus operandi of malware exploit, as it is stated the malware starts with injecting payload into “msinfo32.exe” file. The “msinfo32.exe” is legit windows library which gathers system information to dragonize the system issues.
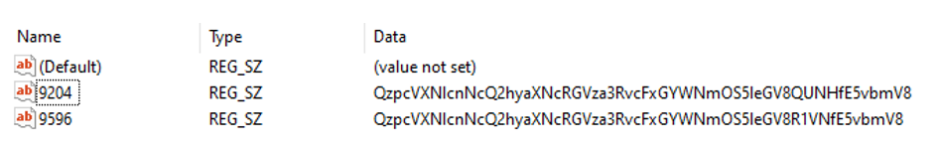
Once the “msinfo32.exe” library gets infected, the malware will start activities like making changes to Windows Registries to become persistence on victim’s Windows machine. Further, the malware will establish with command-and-control server (C2 server) to access additional payloads and instructions.
The below shown is the snapshot of Windows Registries created by the Bandook RAT.
The Bandook RAT Exploit Steps
- Targeting Victim with phishing attack (PDF File)
- Open PDF file and download .7z which is password protected
- Extract the malware from the .7z and infect the msinfo32.exe library
- Manipulate Windows Registries working in shadow of affected library
- Establish communication with Command-and-Control Server (C2)
- Download the additional payloads and instructions from C2 server
- Execute Files and DLL function from C2 server and Control victim machine
- Carry out all the action and fully compromise the victim machine
- Once the work done, kill all processes and uninstall malware
This was the overview of how an attacker can fully compromise the Windows machines using the new variant of Bandook RAT.
Conclusion
The Cybersecurity is the ever growing field. It a challenging tast to cop-up with every single activities. You never know about what will be the next move of Blackhats. To make the cyber space secure, thre should be active competiton between RedTeam and BlueTeam members. Along with that a person should always spend some time reading new attack emerging in market and new modus operandi of hackers by reading blocgs and article on new technologies and their weakness or vulnerabilities.
Hope you like the article and it has helped you in understanding the modus operandi of the Bandook RAT. If want to get information about cyber attacks and cybersecurity, keep visiting our blog – Dhacker Infosec Blogs.
Stay Safe, Stay Secure!!

